If you’ve spotted “content://cz.mobilesoft.appblock.fileprovider/cache/blank.html” in your Android device logs or browser history, you’re probably wondering if your phone has been compromised. This cryptic-looking string can trigger security concerns, especially when you don’t recognise where it came from.
Here’s the reassuring truth: this isn’t malware, spyware, or any form of malicious software. It’s a normal part of how the AppBlock productivity app manages blocked content on your Android device. This content URI represents Android’s sophisticated file management system working exactly as designed.
Understanding what this file does and why it appears can help you feel more confident about your device’s security, whilst giving you valuable insights into how modern Android apps protect your digital wellbeing.
The Quick Answer: It’s Safe and Normal
Explanation: The content://cz.mobilesoft.appblock.fileprovider/cache/blank.html URI is completely legitimate and poses zero security risk to your Android device. This file belongs to AppBlock, a popular productivity application developed by MobileSoft that helps users manage digital distractions by blocking access to time-wasting apps and websites.
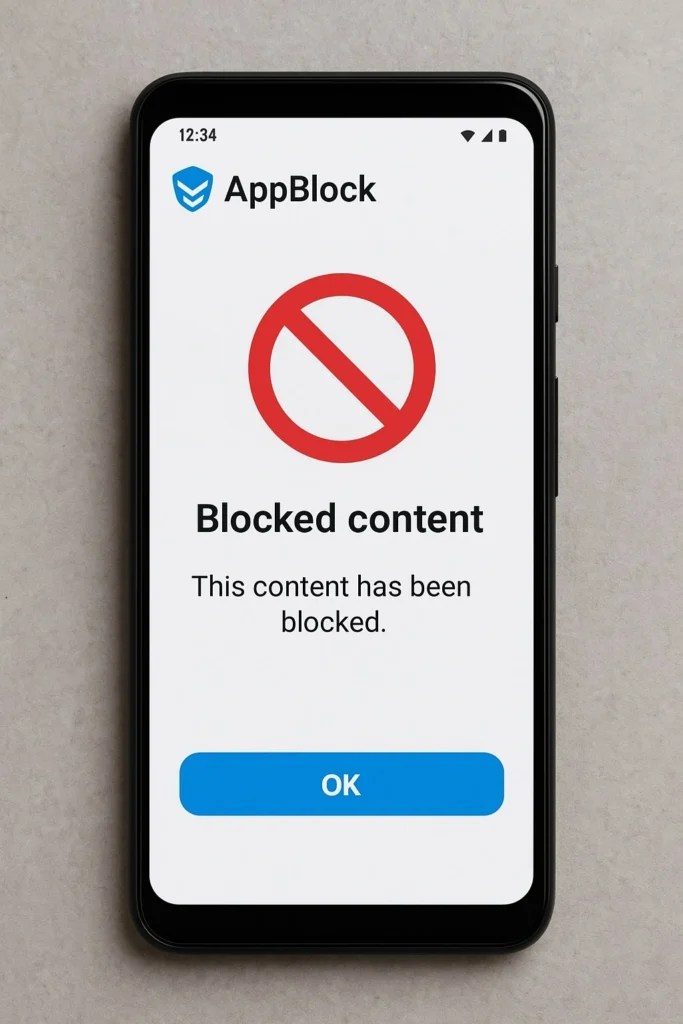
When AppBlock blocks a website or redirects content, it doesn’t simply throw an error message. Instead, it loads a blank HTML page to maintain a smooth user experience. This prevents jarring interruptions whilst ensuring blocked content doesn’t accidentally load in the background.
Example: Imagine you’re using AppBlock during work hours to block social media sites. When you try to visit Facebook, instead of seeing a harsh “BLOCKED” message, AppBlock smoothly redirects you to this blank page. The URI appears in your browser history as a record of this protective action.
This process demonstrates thoughtful app design—protecting your focus without creating frustrating user experiences. The cached blank.html file loads instantly because it’s stored locally on your device, making the blocking process seamless.
Tip: Always check for updates to your mobile application to benefit from the latest features and security enhancements. If you frequently see this URI, it means AppBlock is actively working to protect your productivity. Rather than being concerned, you can feel confident that your digital wellbeing tool, powered by the MobileSoft AppBlock file provider, is functioning properly.
Breaking Down content://cz.mobilesoft.appblock.fileprovider/cache/blank.html
Explanation: Understanding each component of this content URI helps demystify what initially appears to be complex technical jargon. Android uses a structured approach to file management that prioritises security and app isolation.
Let’s decode each part systematically:
- content:// indicates this uses Android’s secure content provider system
- cz.mobilesoft.appblock identifies the specific app (AppBlock by MobileSoft)
- FileProvider is an essential component for sharing files between Android applications securely. refers to Android’s secure file-sharing mechanism
- /cache/blank.html points to a temporary HTML file in the app’s cache directory
Example: Think of this like a postal address system. Just as “123 Main Street, Sydney, NSW” tells Australia Post exactly where to deliver mail, this URI tells Android exactly which app owns this file and where it’s stored.
The “cz” prefix indicates the developer’s country code (Czech Republic), followed by the company name (mobilesoft) and app identifier (appblock). This naming convention ensures no two apps can have identical identifiers.
Tip: You can identify any Android app by looking at its package name structure. Legitimate apps from established developers follow this reverse domain naming convention.
Understanding Android Content URIs
Android content URIs serve as secure pathways for apps to access files without exposing actual file system locations. This approach prevents malicious apps from directly accessing the data of other apps, thereby maintaining strict security boundaries between applications.
Content providers act as gatekeepers, controlling which apps can access specific files and under what circumstances. When AppBlock creates its blank.html file, only AppBlock itself (and authorised system processes) can access it directly through the file provider.
Example: Traditional file systems might use paths like “/data/data/appname/cache/file.html” but Android’s content URI system obscures these details for security.
Tip: Content URIs always start with “content://” – if you see this prefix, you’re looking at Android’s secure file access system in action.
Why “blank.html” Matters
Blank HTML files serve crucial purposes in app blocking scenarios. They provide clean, distraction-free placeholders that prevent visual disruption whilst maintaining browser stability. This approach avoids triggering autoplay scripts, trackers, or other potentially problematic web elements.
The HTML format ensures compatibility with Android’s WebView component, allowing smooth integration within apps that display web content. A blank page loads instantly and consumes minimal system resources.
Example: Instead of displaying error messages that might frustrate users, AppBlock’s blank page creates a zen-like pause that reinforces the blocking intention.
Tip: Many productivity apps use similar blank page strategies—it’s a sign of thoughtful user experience design rather than a technical limitation.
What Is AppBlock and Why Does It Create This File?
Explanation: AppBlock is a legitimate digital wellbeing application designed to help users manage screen time and reduce digital distractions. Developed by MobileSoft, it’s available on the Google Play Store and has helped millions of users improve their productivity and focus with the AppBlock file provider.
The app works by intercepting attempts to access blocked applications or websites, then redirecting users to neutral alternatives. This cache file plays a vital role in that process, providing instant placeholder content without requiring the user to interact with the mobile application. internet connectivity.
AppBlock’s core features include scheduled blocking sessions, app usage analytics, strict mode prevention of bypassing, and location-based restrictions. The blank.html file supports these functions by ensuring smooth operation during content blocking scenarios.
Example: A university student in Melbourne might use AppBlock to block gaming apps during study sessions. When they accidentally tap a blocked game, AppBlock instantly loads the blank page instead of the game’s loading screen, maintaining their focus.
The cached approach means this redirect works even when offline, ensuring consistent protection regardless of internet connectivity. This reliability makes AppBlock particularly valuable for users in areas with spotty mobile coverage across Australia.
Tip: Check the Google Play Store to verify any app’s legitimacy—AppBlock has thousands of positive reviews and regular updates, confirming its trustworthy status.
When and Where You’ll Encounter This URI
Explanation: You might discover this content URI in several common scenarios while using your Android device. Understanding when it appears helps distinguish normal behaviour from potential security concerns.
Most commonly, you’ll see this URI in the browser history after AppBlock redirects blocked websites. System cleaning apps might also flag it during cache scans, and developers might encounter it in debugging logs when analysing app behaviour.
Example: After a productive work session using AppBlock, checking your Chrome history might reveal multiple instances of this URI corresponding to times you attempted to visit blocked social media sites. Each entry represents a successful protection event.
Android’s built-in storage analyzer might also display this file when showing cached data breakdown by app. File manager applications with advanced features could list them among AppBlock’s temporary files.
System diagnostic tools and crash reporting services occasionally capture this URI when logging app interactions, particularly if any unexpected behaviour occurs during content blocking.
Tip: If you see this URI repeatedly at specific times, it indicates AppBlock is actively protecting your focus during those periods—a positive sign that your digital wellbeing strategy is working.
Is This a Privacy or Security Risk?
Explanation: This content URI poses absolutely no privacy or security risk to your Android device or personal data. Android’s robust permission system and app sandboxing ensure that this file remains isolated within AppBlock’s secure environment.
The file contains only blank HTML content—no personal information, browsing data, or sensitive details. It cannot be accessed by other apps without explicit permission, and it doesn’t transmit any data over the internet.
Android’s architecture prevents unauthorised access to app-specific files like this one, thanks to the implementation of a file provider. Even if a malicious app wanted to access this file, it would need specific permissions that users must explicitly grant, ensuring that the app development follows secure practices.
Example: Think of this like a private note in your locked diary—other people can’t read it without your permission, and even if they could, it’s just a blank page with no sensitive information.
Here’s a simple security checklist for evaluating any suspicious files: • Does the file belong to a legitimate app from the Google Play Store? • Is the app developer reputable with positive reviews? • Does the file path include recognisable app identifiers? • Are you experiencing any unusual device behaviour?
For this specific URI, all answers indicate normal, safe operation.
Tip: Download AppBlock only from the official Google Play Store to ensure you’re getting the legitimate version with proper security measures.
Red Flags vs. Normal Behaviour
Normal AppBlock behaviour includes occasional appearance of this URI in browser history, temporary storage in app cache, and automatic cleanup when cache is cleared. The file should never contain actual content or personal information.
Red flags would include similar URIs from unknown apps, files that persist after uninstalling AppBlock, or URIs that attempt to access sensitive device areas outside the app’s designated sandbox, highlighting the importance of understanding content URIs.
Example: A legitimate AppBlock URI always includes “cz.mobilesoft.appblock” in the path. If you see similar patterns with different app names you don’t recognise, investigate further.
Tip: When in doubt, uninstall and reinstall AppBlock from the Play Store—this removes all cached files and ensures you have the latest secure version.
Troubleshooting Common Issues
Explanation: While this content URI rarely causes problems, understanding how to address potential issues empowers you to maintain optimal device performance. Most problems relate to cache accumulation rather than security concerns.
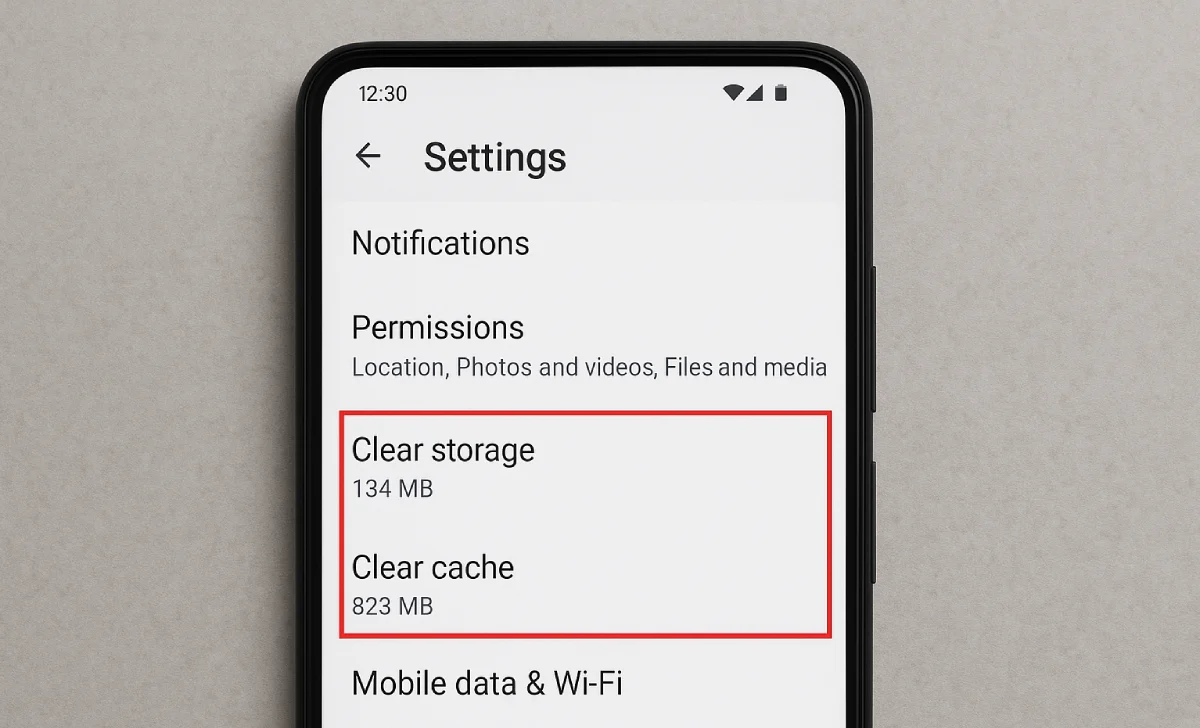
If AppBlock seems sluggish or the blank page isn’t loading properly, clearing the app’s cache often resolves these issues. This process removes temporary files, including blank.html, allowing AppBlock to recreate fresh versions.
Occasionally, system storage constraints may prevent the creation of proper cache files, leading to error messages when AppBlock attempts to redirect blocked content. Freeing device storage typically resolves these scenarios.
Example: If AppBlock’s blocking feature stops working smoothly, follow these steps:
- Open Android Settings > Apps > AppBlock
- Tap “Storage” > “Clear Cache”
- Restart AppBlock
- Test blocking functionality
For persistent issues, consider updating AppBlock through the Play Store or restarting your device to clear any temporary system conflicts.
Tip: Set a monthly reminder to clear the cache for all apps—this maintenance practice keeps your device running smoothly and prevents cache-related issues.
Best Practices for Managing App Cache and Security
Explanation: Maintaining healthy cache management practices and security awareness protects your device while ensuring optimal app performance. Regular maintenance prevents accumulated temporary files from consuming excessive storage space.
Implement a routine of reviewing app permissions monthly, particularly for productivity apps like AppBlock that require broad access to function effectively. Understanding which permissions each app uses helps you make informed decisions about your digital security.
Download apps exclusively from official sources like the Google Play Store, which provides automated security scanning and developer verification. This practice significantly reduces risks from malicious software disguised as legitimate applications.
Example: Create a monthly digital maintenance routine: • Clear cache for frequently used apps • Review and update app permissions • Check for app updates in Play Store • Remove unused applications • Verify no suspicious files in downloads folder
Monitor your device’s behaviour for any unusual patterns, such as unexpected battery drain, unfamiliar network activity, or mysterious files appearing in storage directories.
Tip: Enable Google Play Protect in your Play Store settings—this automated security feature continuously scans installed apps for potential threats and provides real-time protection.
Regularly back up important data to cloud services, ensuring you can quickly recover if any security issues require a device reset. This preparation provides peace of mind whilst using productivity tools like AppBlock.
Conclusion
The content://cz.mobilesoft.appblock.fileprovider/cache/blank.html URI represents Android’s sophisticated approach to app security and user experience design, not a threat to your device. This technical-looking string demonstrates how modern mobile operating systems balance functionality with robust security measures.
By understanding these technical elements, you’re better equipped to maintain your digital privacy and make informed decisions about the apps you use. AppBlock’s use of cached blank pages showcases thoughtful development that prioritises both user experience and system security.
Rather than fearing unfamiliar technical terms, embrace the opportunity to learn how your device protects you. Share this knowledge with other Android users who might encounter similar concerns, and continue exploring the fascinating world of mobile security.
Have you encountered this URI on your device? Share your experience in the comments below and help other Australian Android users understand their device’s security features better.

